The Stack behind Candide Mobile Wallet
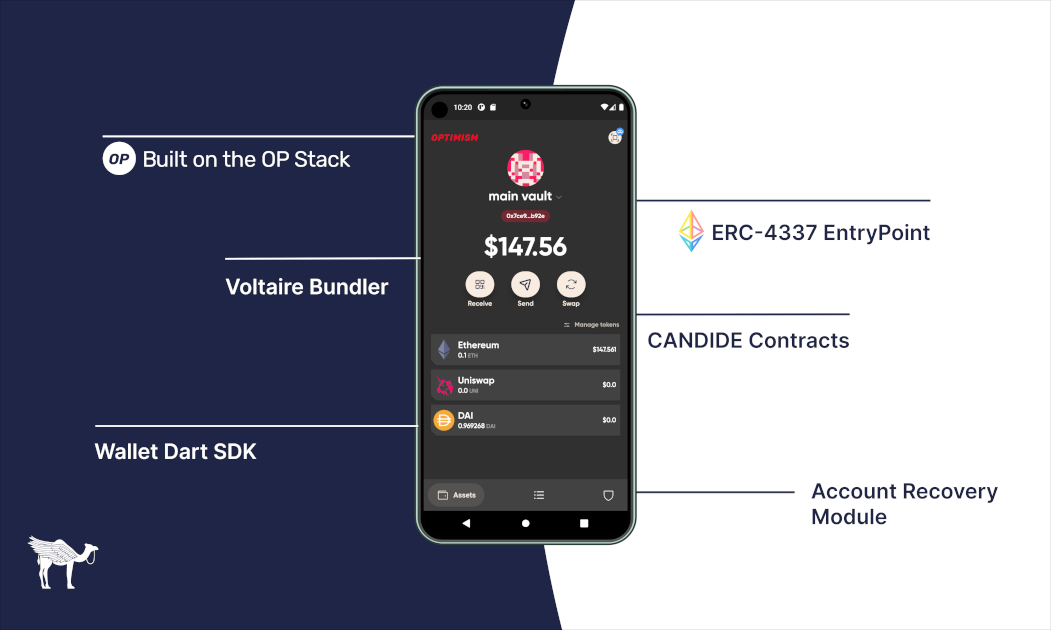
Candide Wallet is an open-source, secure, self-custodial Smart Wallet built on ERC-4337. It leverages account abstraction without compromising on decentralization and censorship resistance. In practical terms, this means a Smart Wallet that doesn't depend on a centralized relayer controlled by a single entity. A gateway to undeniable free access to Ethereum for anyone with a smartphone and internet access.




